La fin de l’assistance windows 10 est le 14 oct. 2025. Êtes-vous prêt?
Microsoft mettra fin à l’assistance pour Windows 10 le 14 octobre 2025, ce qui signifie qu’il n’y aura plus d’assistance technique, de correctifs de sécurité, ni de mises à jour automatiques de Windows. Votre organisation est-elle prête ? Portez le Évaluation de la préparation en fin de soutien de Windows 10 dès aujourd'hui.
What are Computer Security Policies for Businesses and Why are They Important?
Businesses face an ever-growing array of cybersecurity threats. From ransomware attacks to phishing schemes, the risks are pervasive and can lead to devastating consequences, including financial losses, reputational damage, and legal liabilities. To mitigate these risks, businesses must implement comprehensive computer security policies. These policies serve as a framework for safeguarding sensitive information, ensuring compliance with regulations, and maintaining operational continuity.
Computer security policies are not just technical documents; they are strategic tools that align cybersecurity practices with business objectives. They define the rules, procedures, and responsibilities for employees, contractors, and stakeholders, ensuring everyone understands their role in protecting company assets. This article explores the key components of computer security policies, their importance, and best practices for implementation.
Key Components of Computer Security Policies
Access Control Policies
Access control is often considered a cornerstone of computer security because it defines who is permitted to use specific systems, applications, and data within an organization. These policies are structured to ensure that access is organized and aligned with business roles and responsibilities.
- Role-based access control (RBAC): Permissions are assigned based on job roles, which can help ensure that employees only interact with resources relevant to their responsibilities.
- Least privilege principle: Users are restricted to the minimum resources needed to complete their work, which supports both security and efficiency.
- Authentication methods: Strong password rules, multi-factor authentication, and biometric verification are typically included, which can strengthen the reliability of identity checks.
By applying these approaches, access control policies could help safeguard sensitive information and reduce the likelihood of breaches or insider threats.
Data Protection Policies
Data protection policies define the way sensitive information is stored, transmitted, and processed within an organization. These measures are designed to align with security standards while supporting compliance and operational needs.
- Encryption standards: Data is encrypted at rest and in transit, which can help ensure confidentiality and reduce risks of interception.
- Data classification: Information is categorized by sensitivity levels, such as public, confidential, or restricted, which allows businesses to apply the right level of protection.
- Backup procedures: Critical data is backed up on a regular basis, which supports recovery efforts and helps minimize disruption in the event of a cyber incident.
When applied consistently, data protection policies could safeguard intellectual property, customer information, and financial records from unauthorized access or loss.
Incident Response Policies
Incident response policies establish a structured framework for addressing cybersecurity incidents in an organized manner. These measures are designed to ensure that businesses respond quickly and effectively when threats occur.
- Incident detection: Systems are monitored for unusual activity, which can help identify unauthorized access or malware before damage escalates.
- Reporting procedures: Clear reporting guidelines are outlined so incidents can be escalated to the right teams, which supports faster resolution.
- Recovery plans: Steps are documented for restoring systems and data, which helps maintain continuity and minimize disruptions after an attack.
By following structured incident response policies, organizations could reduce downtime and lessen the overall impact of cybersecurity threats on operations.
Acceptable Use Policies (AUP)
Acceptable use policies define how employees can use company-owned devices, networks, and software. These policies often include:
- Prohibited activities: Listing activities such as downloading unauthorized software, accessing inappropriate websites, or sharing sensitive information.
- Device management: Guidelines for using personal devices for work purposes (e.g., Bring Your Own Device policies).
- Monitoring and enforcement: Explaining how compliance will be monitored and violations addressed.
AUPs help prevent misuse of company resources and reduce the risk of security vulnerabilities.
Training and Awareness Policies
Training and awareness policies are designed to reduce risks associated with human error, which is often a significant factor in cybersecurity incidents. These initiatives aim to equip employees with knowledge and practical skills that support organizational security.
- Recognizing phishing attempts: Employees are taught how to identify suspicious emails or links, which can help reduce the likelihood of successful attacks.
- Password hygiene: Guidance is provided on creating strong, unique passwords, which supports stronger access control practices.
- Reporting suspicious activity: Staff are encouraged to report unusual behavior or potential threats, which enables quicker responses to security issues.
By implementing ongoing training and awareness programs, employees could serve as the first line of defense and contribute to a stronger overall security posture.
Why Businesses Need Computer Security Policies
Protecting Sensitive Information
Businesses handle vast amounts of sensitive information, including customer data, financial records, and proprietary intellectual property. Without robust security policies, this data is vulnerable to theft, manipulation, or exposure. A single data breach can result in significant financial losses and irreparable damage to a company's reputation.
Ensuring Regulatory Compliance
Many industries are subject to strict regulations governing data protection and cybersecurity. Examples include the General Data Protection Regulation (GDPR) for businesses operating in Europe and the Health Insurance Portability and Accountability Act (HIPAA) for healthcare organizations. Security policies help businesses comply with these regulations, avoiding costly fines and legal consequences.
Mitigating Financial Risks
Cyberattacks can lead to direct financial losses, such as ransom payments or theft of funds. Additionally, businesses may face indirect costs, including legal fees, customer compensation, and lost revenue due to downtime. Security policies reduce the likelihood of such incidents, protecting the company's bottom line.
Enhancing Operational Continuity
A cyberattack can disrupt business operations, causing delays and reducing productivity. Security policies ensure systems are resilient to attacks and can recover quickly, minimizing downtime and maintaining operational continuity.
Building Customer Trust
Customers expect businesses to protect their personal information. Implementing and enforcing security policies demonstrates a commitment to cybersecurity, fostering trust and loyalty among customers.
Best Practices for Implementing Computer Security Policies
Strengths
Comprehensive Coverage: Security policies should address all aspects of cybersecurity, from access control to incident response. This ensures no vulnerabilities are overlooked.
Employee Involvement: Engaging employees in the development and implementation of policies fosters a culture of security awareness.
Regular Updates: Cyber threats evolve rapidly, so policies must be reviewed and updated regularly to remain effective.
Clear Communication: Policies should be written in clear, concise language that is easy for employees to understand and follow.
Integration with Business Goals: Security policies should align with the company’s overall objectives, ensuring they support rather than hinder business operations.
Drawbacks
Implementation Challenges: Developing and enforcing security policies can be time-consuming and resource-intensive, particularly for small businesses.
Resistance to Change: Employees may resist new policies, especially if they perceive them as restrictive or inconvenient.
Complexity: Overly complex policies can confuse employees and lead to non-compliance.
Cost Implications: Implementing certain security measures, such as advanced encryption or multi-factor authentication, may require significant investment.
Monitoring and Enforcement: Ensuring compliance with policies requires ongoing monitoring, which can strain resources.
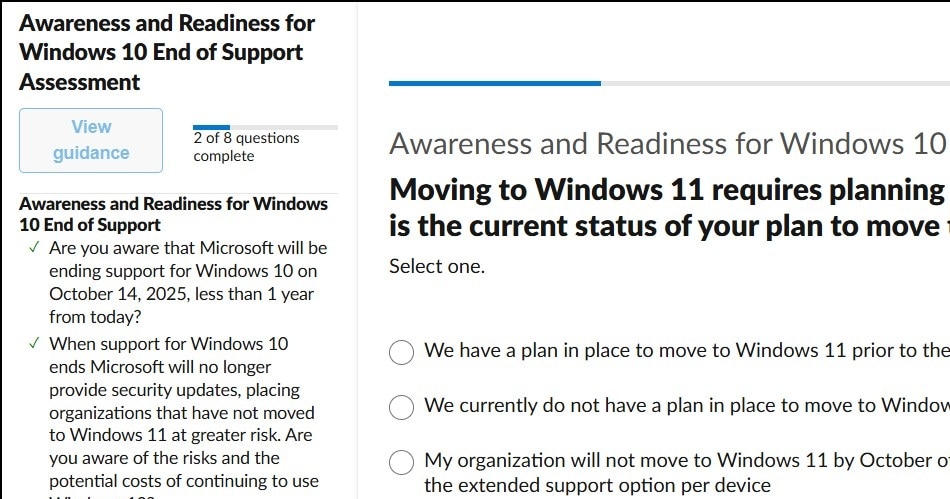
Y a-t-il un outil pour m’aider à tester par la compatibilité de Windows 10 EOS (fin de l’assistance) ?
Oui, vous pouvez utiliser le Sensibilisation et préparation pour Windows 10 Fin de l’assistance outil d’évaluation. [Si votre navigateur ne vous mène pas directement à l’outil, faites défiler la page jusqu’à son emplacement au bas de la page.] Il s’agit d’un questionnaire simple, simplement de questions à choix multiples, pour tester votre préparation et celle de votre entreprise à passer de Windows 10 à Windows 11. Après avoir terminé, vous obtiendrez une évaluation des risques et des conseils sur les prochaines étapes.
Why are access control policies important?
Access control policies define who is allowed to access systems, applications, and data. By limiting access based on responsibilities, these policies help ensure employees only use the resources they need. This approach could reduce the risk of breaches and insider threats.
What is the least privilege principle?
The least privilege principle grants users the minimum level of access required to perform their tasks. This method ensures sensitive systems and data remain protected from unnecessary exposure. Applying it consistently could minimize both accidental and malicious risks.
How does encryption protect sensitive data?
Encryption converts information into a format that cannot be read without the proper keys. This means data remains secure whether stored locally or transmitted across networks. For businesses, encryption could be vital in maintaining confidentiality and protecting customer trust.
What are incident response policies?
Incident response policies outline structured steps for detecting, reporting, and recovering from security incidents. They ensure that organizations have clear guidelines during a cyber event. With effective execution, these policies could minimize downtime and reduce the overall impact of threats.
What is an acceptable use policy (AUP)?
An acceptable use policy explains how employees should use company-owned devices, networks, and software. It sets boundaries that prevent misuse and protect organizational resources. By following an AUP, businesses could reduce vulnerabilities and promote responsible use of technology.
Why is employee training essential for cybersecurity?
Employee training focuses on building awareness of phishing, password safety, and reporting suspicious behavior. Regular sessions help staff understand their role in safeguarding information. With proper training, employees could serve as a strong first line of defense against cyber threats.
How do security policies ensure regulatory compliance?
Security policies incorporate guidelines for protecting data, controlling access, and managing incidents. These measures align with standards set by regulations such as GDPR or HIPAA. By following them, businesses could meet compliance obligations and avoid penalties.
What are the financial risks of poor cybersecurity?
Weak security practices can create vulnerabilities that lead to financial losses. Expenses may include legal fees, recovery costs, or compensation for affected customers. With strong policies in place, organizations could reduce these risks and protect revenue.
How do security policies enhance operational continuity?
Security policies ensure that systems are prepared to resist cyberattacks and recover quickly when issues occur. They establish procedures that keep operations running smoothly. With this preparation, businesses could maintain productivity even during disruptions.
What is role-based access control (RBAC)?
Role-based access control assigns permissions according to specific job roles. Employees receive access only to the systems and resources needed for their tasks. This structure could simplify management while improving security.
How can businesses monitor compliance with security policies?
Compliance can be tracked through audits, automated monitoring tools, and employee reporting. These methods help organizations verify that policies are being followed. When applied regularly, monitoring could reduce risks and strengthen accountability.
How often should security policies be updated?
Security policies are typically reviewed on a regular basis to address new threats and evolving business needs. Updates may include changes in regulations, technology, or workflows. By refreshing them consistently, businesses could stay prepared for modern risks.
What is data classification?
Data classification organizes information into categories such as public, confidential, or restricted. This approach ensures sensitive data receives higher levels of protection. For businesses, classification could help prioritize security efforts effectively.
How do backup procedures support data protection?
Backup procedures involve saving copies of critical information on a routine schedule. These backups ensure data can be restored in case of cyberattacks or hardware failures. With reliable backups, businesses could recover faster and prevent permanent loss.
Why is clear communication important for security policies?
Clear communication ensures employees understand their responsibilities and the reasoning behind policies. It reduces confusion and helps establish consistency across teams. When policies are well communicated, compliance could improve significantly.
Qu’est-ce que l’authentification à facteurs multiples ?
Multi-factor authentication requires verification through two or more methods, such as passwords, tokens, or biometrics. This adds a layer of security beyond simple login credentials. By using MFA, businesses could make it harder for attackers to gain unauthorized access.
How do security policies build customer trust?
Strong security policies demonstrate a business's commitment to protecting customer information. When customers see their data handled responsibly, trust and loyalty often increase. Over time, this trust could translate into stronger relationships and brand reputation.
What is the role of monitoring in cybersecurity?
Monitoring involves tracking systems for irregular behavior, unauthorized access, or signs of malware. It provides early detection of threats before they escalate. With active monitoring, businesses could respond quickly and reduce potential damage.
Computer security policies are essential for businesses to protect sensitive information, ensure regulatory compliance, and mitigate financial risks. By implementing comprehensive policies and fostering a culture of cybersecurity awareness, businesses can safeguard their assets and maintain operational continuity. While challenges exist, the benefits far outweigh the drawbacks, making security policies a critical component of modern business strategy.